PWN day 15
A safe practice is passing pointers with a size. Often this leads to a control hijack
ASLR -> Protection against a control flow hijack by randomizing layout of address space
One new thing learned is every process a parent forks off will copy its canary to the child
As mentioned before, pages are always aligned by 0x1000
That means to overwrite a page offset could be done by 2 bytes
Uninitalized Data-> Basically uncleaned data from the stack
Deallocating a stack frame doesnt wipe data
I mention this because a challenge I am working on is storing a memory value I need to retrieve.

In this case it is the ABCDEG

In vararg I can see if I dump more of my addresses I can see the goal value
After looking a bit more, I can of course take advantage of the printf vulns and do just format strings
Moving on to the next challenge

The first thing I noticed is its creating a stack frame of size 0x90 bytes

Next there is a variable with size 0x60 bytes

I see this read takes in 0x1000 bytes
So basically all i have to do to solve this is write a simple bin/zsh shellcode to maintain priv of the file im executing, then redirect my ret address to the buffer of the shellcode.
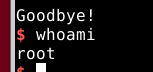
Then I get root. This would not work with bin/sh. Only with zsh
